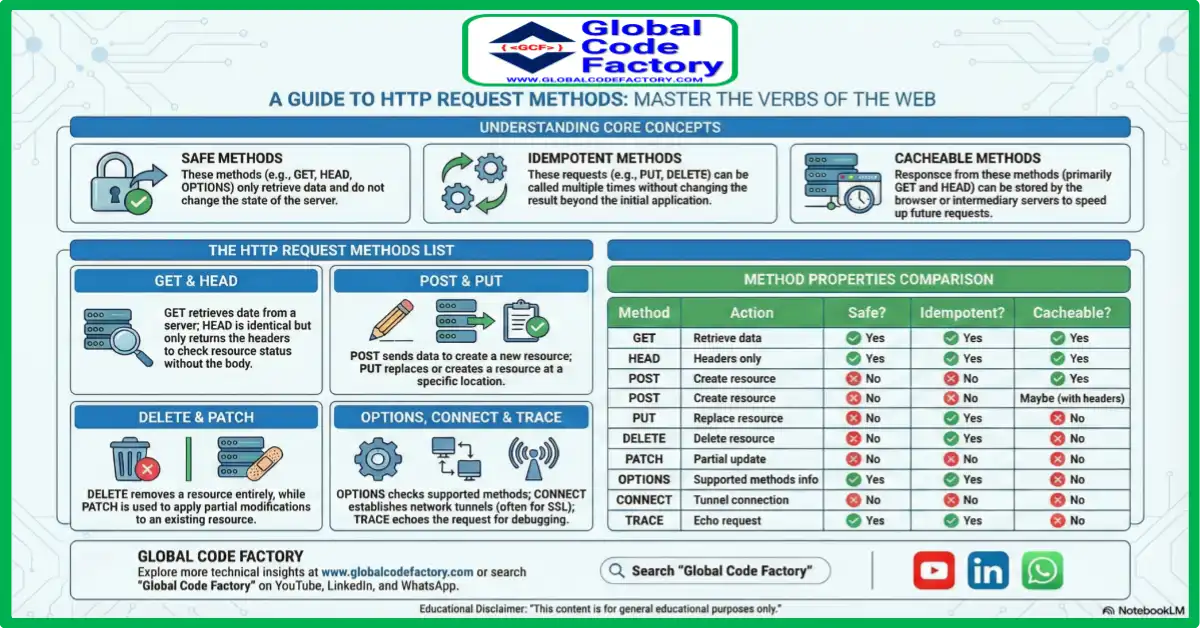
HTTP Request Methods List: An Overview
HTTP Request Methods define the specific action a client wants to perform on a resource. In this guide, we list all key HTTP Request methods, explain their uses, and clarify concepts like safety and idempotency.
What Are HTTP Request Methods?
HTTP stands for Hypertext Transfer Protocol. These request methods—also known as HTTP verbs—tell the server what to do. Common methods include GET, POST, PUT, DELETE, PATCH, OPTIONS, and HEAD. Each method has its purpose, safety characteristics, and support in REST APIs.
List and Meaning of HTTP Request Methods
Firstly, here are the most common methods and their meanings:
1. GET
- Retrieves data from the server without modifying it.
- Safe, cacheable, and idempotent.
2. HEAD
- Similar to GET but returns only headers.
- As a result, Useful for checking resource status.
3. POST
- Sends data to the server to create a resource.
- It is neither safe nor idempotent.
4. PUT
- Replaces or creates a resource at the specified location.
- Therefore, It is idempotent.
5. DELETE
- Removes a resource.
- It is idempotent but not safe.
6. PATCH
- Applies partial modifications to a resource.
- Neither safe nor idempotent by default.
7. OPTIONS
- Returns supported HTTP methods for a resource.
- Equally important, it is safe and idempotent.
8. CONNECT
- Establishes a tunnel to the server, often for SSL.
- In contrast, it is not safe or idempotent.
9. TRACE
- Echoes the received request; helpful for debugging.
- For this reason, it is safe and idempotent.
Cacheability, Idempotency, and Safety
When creating APIs, these qualities are crucial:
- Safe Methods (e.g., GET, HEAD, OPTIONS, TRACE) don’t change server data.
- Idempotent Methods (e.g., GET, HEAD, PUT, DELETE, OPTIONS, TRACE) can be repeated without changing the state beyond the initial request.
- Cacheable Methods include GET, HEAD, and sometimes POST with specific headers.
As a result, understanding these characteristics improves the dependability and design of APIs.
Why HTTP Request Methods List Matters
To illustrate, developers must utilize the appropriate HTTP method to match expected action. For instance, POST submits or creates resources, while GET safely retrieves data. The proper application of these techniques is crucial to REST architecture.